Activism and BDS Beat 27 March 2017
Whoever was behind a cyber attack on the UK’s Palestine Solidarity Campaign earlier this month defaced its social media in the name of an Israeli spy agency, it has emerged.
The attack was reported to police, the campaign said in a statement.
A spokesperson for the campaign has provided The Electronic Intifada with new details about the attack.
On 8 March, the campaign’s Twitter and Facebook accounts were both compromised.
The attacker began posting messages on Twitter, congratulating Palestinian armed resistance and political movement Hamas and its new leader in Gaza, Yahya Sinwar.
The first tweet said it was “looking forward” to “working fondly” with Sinwar. “Together we will build a more supportive UK,” the second tweet read, next to a photo of Sinwar.
Minutes later, the spokesperson said, the team noticed the tweets, deleted them, and tweeted to announce they had been hacked.
But the unknown attacker then deleted that announcement and continued tweeting messages of support for Hamas. PSC then deactivated its Twitter account to investigate how the attacker had gained access. It remained offline for two days.
The Electronic Intifada has been told technical details of the attack but is withholding them for security reasons.
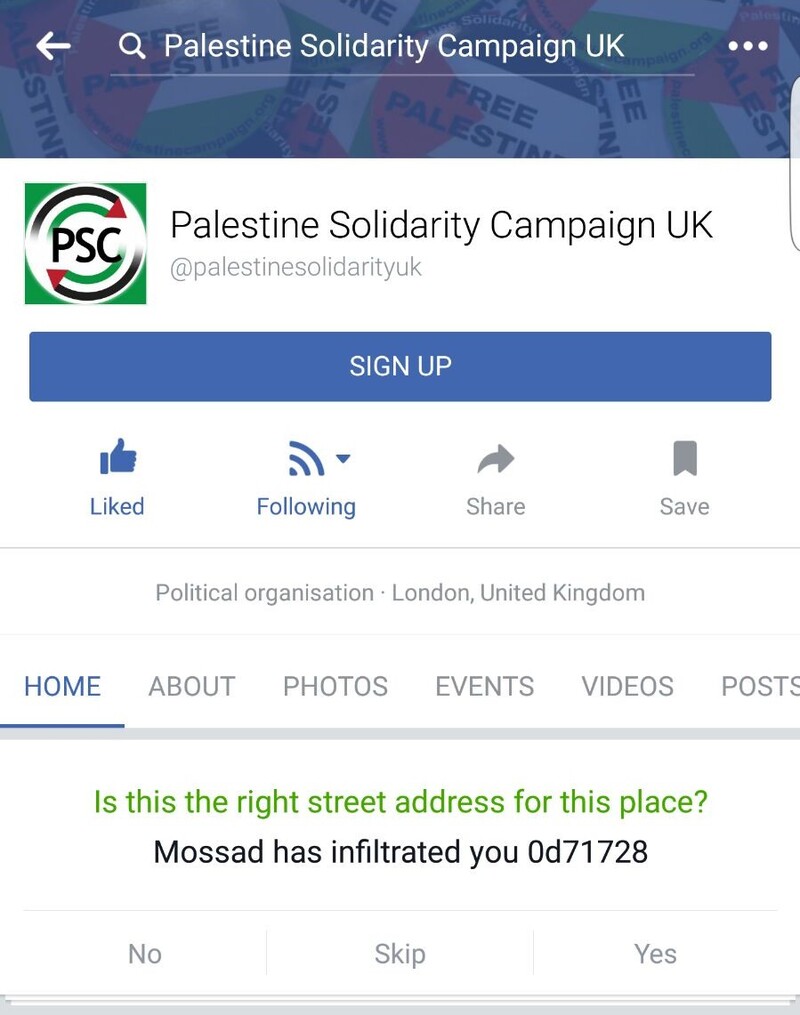
Later the same day, the PSC Facebook account was also hacked, with the page being defaced with the claim that “Mossad has infiltrated you.”
Mossad is Israel’s overseas spying and assassination agency, notorious for a long string of killings, kidnappings and torture.
Tipped off
PSC in a statement reiterated its longstanding policy of non-partisanship. It does not endorse any political party, including Hamas.
The first pro-Hamas tweet was dated 12:25 pm. Anti-Palestinian activists on Twitter soon picked up on the tweets.
A search using the link for the now-deleted tweet shows that the first Twitter user to post it was Russell Langer, a former officer with the Israel-funded Union of Jewish Students.
“I’m honestly not sure if they’ve been hacked,” he wrote, but still criticized PSC for supporting “a terrorist organization.”
Langer reacted to the pro-Hamas tweet just eight minutes after it was posted. There is evidence that the attacker posing as PSC was aware of Langer and may have contacted him directly.
The PSC spokesperson told The Electronic Intifada that a saved draft of a tweet had been addressed to Langer, and to the @HamasInfoEn account. But it was discovered before it could be posted.
Whoever was behind the attack clearly wanted to make sure anti-Palestinian activists were immediately informed of the pro-Hamas tweets before PSC could take back full control of its account.
Langer was one of three pro-Israel activists revealed in undercover footage filmed by Al Jazeera to have held “little secret purpose meetings” aiming to overthrow National Union of Students president Malia Bouattia. Bouattia is a high-profile supporter of BDS, the boycott, divestment and sanctions movement in support of Palestinian rights.
The second anti-Palestinian figure to react rapidly was Michael Freeman, the Israeli embassy’s head of “civil society affairs.”
Just nine minutes after the first pro-Hamas tweet appeared, he reposted it, claiming that PSC had revealed its “true colors” by “partnering” with Hamas.
Footage shot by Al Jazeera as part of its January documentary The Lobby showed that Freeman discussed hiring undercover reporter “Robin” – who had been posing as a pro-Israel activist within the Labour Party – “to work on the whole BDS piece, doing research into the different BDS movements, who they are, what they are.”
The Zionist Federation posted screenshots of the pro-Hamas tweets about 40 minutes after they were made.
But the screenshots appear not to have been taken in the UK’s time zone – the timestamp on the pro-Hamas tweets in the screenshots are two hours ahead of when the original tweets were made.
One possible explanation: the screenshot could have been taken in Israel, where the time zone is two hours ahead of the UK.
Smear campaign
Hamas won elections to lead the Palestinian Authority in 2006. But it is also involved in armed resistance against Israeli occupation forces. It has been outlawed as a “terrorist” organization in the UK and other countries whose governments support Israel.
A long-running theme of Israeli propaganda has been to treat campaigning groups like PSC that support BDS, as part of a “terrorist” conspiracy led by groups like Hamas.
Tel Aviv’s Reut Institute advocates an “attacking” and “sabotage” campaign against what it terms the “red-green alliance” of left-wing and Muslim groups.
The likely motive for this cyber attack on PSC was to discredit the group as being close to a violent “terrorist” organization.
Last year, the Tel Aviv newspaper Haaretz reported that Israel had established a “dirty tricks” or “tarnishing” unit to target BDS groups.
Only a few days after the attack, PSC chair Hugh Lanning was detained and denied entry when he flew into Tel Aviv airport.
Lanning told The Electronic Intifada that during his interrogation he was presented with a photo of himself at a press conference during a 2012 trip to Gaza, standing in a group that included Hamas lawmaker Khalil al-Hayya.
A photo from the same trip of Lanning meeting Gaza prime minister Ismail Haniyeh, a Hamas leader, was used by whoever perpetrated the cyber attack on the PSC Twitter account. One of the pro-Hamas tweets included the photo.
The photo has long been used and taken out of context by anti-Palestinian attack blogs.
The Jewish Chronicle reacted to Israel’s ban on Lanning by claiming that PSC’s account “was temporarily suspended after a message posted from it welcomed new Hamas leader Yahya Sinwar.”
The Israeli embassy told other media that Lanning “is associated with the leaders of Hamas, which is designated as a terror group.”
An Israeli embassy spokesperson also circulated the same photo as that used in the hack.
Israeli cyber crime
Israel or its surrogates have a long history of online criminality targeting journalists, activists and states.
Last year, online security service eQualit.ie analyzed six major attacks on the website of the Palestinian BDS National Committee and concluded that Israel may have been directly involved.
In 2014, The Electronic Intifada was among several Palestine-focused news sites forced offline for hours after massive distributed denial of service attacks.
At perhaps its most extreme, Israeli cyber warfare sabotaged Iran’s nuclear energy program. The Stuxnet virus, which caused physical damage, was created by Israel and the US government.
In 2012 the Flame malware, also thought to have been created by Israel, was discovered to have been spying on thousands of computers across the Middle East.
More recent threats against Palestine campaigners come in the context of Israel’s increasingly desperate war against BDS.
Only days before the 2016 report about attacks on the BDS National Committee’s website was published, a top Israel lobbyist told an anti-BDS conference hosted by Israel in New York that “the war on social networks is important.”
“All I will say here is that these ideas do not remain ideas,” he added. “We are already beginning to implement them.”





